Authenticating a signature helps verify the validity and legality of documents. There are several ways to do this, including implementing advanced authentication technologies such as ID verification, biometrics, and digital certificates.
That said, it is vital to verify signatures to avoid fraud and speed up the process of completing paperwork. Here’s everything you need to know about electronic signature authentication and its importance in today’s digital age.
Table of Contents

Can Electronic Signatures be Verified?
Yes, certainly. Most eSignature platforms offer built-in verification tools to guarantee the authenticity of an electronic signature.
For example, Fill has a signer identity verification functionality that requires signers to upload a copy of any government-issued ID and undergo a selfie check. This ensures that only authorized individuals can access and sign the documents. This is a surefire way to prevent breaches and forgery.
Additionally, other electronic signature software uses other signature authentication methods, such as email verification, unique signer codes, and audit trails, to provide a secure and traceable signing process. This level of verification gives peace of mind to both the sender and the recipient, knowing that the signed document is authentic and legally binding.
What Is Signature Authentication?
Signature authentication is a process used to verify a person or entity’s identity based on their digital signature. It helps confirm whether the signatory is actually the person they claim to be. It is also used to verify the document’s authenticity, ensuring that no tampering has occurred and that the information contained within the document is accurate and valid.
Through electronic signature authentication, businesses can ensure compliance with the regulatory requirements set by the E-Sign Act and other government regulations.
7 Methods for Authenticating Electronic Signatures
1. Basic authentication
This method involves asking the signer to provide valid credentials such as a username and password. This way, individuals and entities can quickly identify themselves by providing their unique login credentials. Doing so will also allow them to access their online dashboard, wherein they can preview documents and freely affix their signatures on agreements and forms.
2. Email authentication
Email authentication is a method of verifying the signer’s identity through sending confirmation links to the recipient’s email inbox. Clicking the link confirms that the email is active. It also shows that the signer indeed has access to the email address provided.
3. Knowledge-based authentication (KBA)
This method involves asking signers questions based on the personal information provided upon application. Only after giving the correct answers will the signer be able to proceed and affix their signatures onto the agreements and forms. Examples of knowledge-based authentication questions are:
- What is your mother’s maiden name?
- What is the name of your first pet?
- What is your place of birth?
- What is your library card number?
- What is your frequent flyer number?
It is also important to note that KBA is generally less secure than multi-factor authentication. Unauthorized users can still gain access to an account if they can correctly answer the questions through guessing, social engineering, or by using any publicly available information.
4. Biometric authentication
Similar to the methods mentioned above, biometric authentication aims to validate whether a signer is who they claim to be. It uses unique physical or behavioral characteristics to confirm a signer’s identity. Examples of biometric factors include fingerprints, facial recognition, voice recognition, and iris and retina scans.
5. Two-factor authentication
This method provides an additional layer of security because even if an attacker knows the password, they will still be asked to input a two-factor authentication code. Only the signer can access or generate the two-factor (2FA) code via SMS or app.
6. Digital certificates
This method uses digital certificates and encryption to bind electronic documents to individuals or entities. Digital certificates often include information such as the certificate holder’s identity, the certificate’s expiration date, and the issuer’s digital signature. Through this, it will be easier to verify the authenticity of the electronic document. You can also feel confident that it comes from a trusted source.
7. Signer ID verification
Signer ID Verification is a process that prompts signers to confirm their identities, either through a biometric check or by providing a government-issued ID. Doing so helps prevent fraudulent activities such as identity theft and impersonation. It helps assure that the person signing is who they say they are and is legally authorized to do so.
It’s also worth noting that countries like the US and Europe have specific regulations on which methods of eSignature authentication are legally binding. Industries, like those in healthcare and legal, also have specific standards as to what constitutes a valid signature. It’s always best to check whether your electronic signature authentication process meets the legal requirements for the industry and country in which you operate.
Electronic Signature Authentication Benefits
Having signers undergo the authentication process provides several benefits, including:
- Convenience: Electronic signatures allow individuals to sign documents from anywhere, at any time, as long as they have internet access. This eliminates the need for physical mail or in-person meetings to obtain signatures, making the process faster and more convenient.
- Cost Savings: Electronic signatures can significantly reduce the costs associated with printing, mailing, and storing physical files. It can also reduce the need for expensive in-person meetings.
- Security: Electronic signatures use encryption and other security features to protect the authenticity and integrity of the signed document. Not only does this help prevent fraud, but it also provides a legally binding way to sign documents electronically.
- Compliance: Electronic signature solutions can provide a tamper-proof, secure, and auditable record of the signature process, allowing organizations to meet regulatory requirements, including those set by HIPAA and GLBA.
- Speed and Efficiency: Electronic signature allows for faster execution of documents and agreements, enabling organizations to move forward with business operations more quickly.
All in all, electronic signature authentication can be a great tool to streamline document management.
How to Validate an eSignature Using Fill
Using Fill to ensure the authenticity and validity of an electronic signature is easy. Here’s what you need to do:
- Login with your Fill account.
- Click Start Now, then select Request Signature to send an electronic signature request to one or more signers.

- Upload a document or select an existing template from the gallery.
- Enter the email, first name, and last name of your signer.
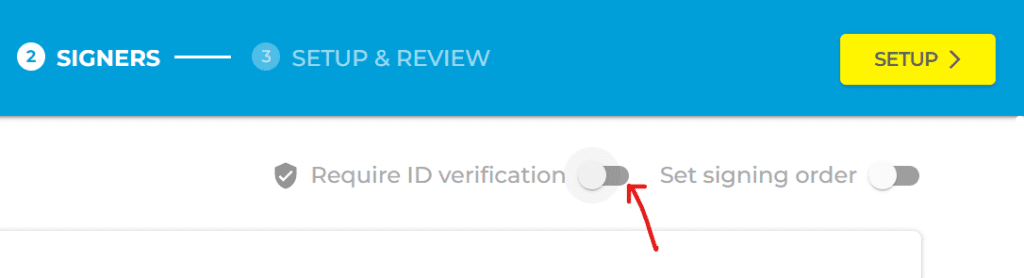
- You should see a toggle button right next to Require ID verification. Click on it to enable the option for verifying a signer’s identity. Note: You need at least one credit to initiate the process. You can purchase credit by clicking Add Credits. One credit is good for one signer identity verification request.
- Click Setup and proceed to complete the necessary preparations for your eSignature request. You can modify existing fields from templates or add custom fields on a blank page.
- Click Review to double-check the details.
- Once everything is all set, click Send.
Your recipient should receive a request asking to sign a document, but before they can do so, they must first go through the identity verification process. The entire process should only take several minutes. Once done, they will be able to sign the document securely.
Integrate Identity-Proofing Into Your eSignature Workflow
Keeping up with modern times is a must, especially if you want to stay competitive in the business world. With electronic signature authentication, you can eliminate the need to verify signatures manually. You can also save time and money by streamlining your document signing process, allowing signatories to sign from anywhere at any time.
Don’t wait until it’s too late. Make security a top priority. Fill’s signer ID verification feature guarantees a secure and effortless signing process that meets the highest security standards.
Sign up for an account today to keep your documents safe from unauthorized access.










