SAML Single Sign-On
Security Assertion Markup Language (SAML) is an XML-based framework for enabling authentication through a third party identity provider or in-house single sign-on application.
SAML comes in handy for organizations which use multiple applications or services and need a single source to manage member activity. Instead of creating multiple credentials for different applications, with SAML you can create one set of credentials per member and allow them to access multiple applications.
SAML offers the ability to:
- Manage a password policy across multiple applications
- Access multiple applications securely
- Reduce the risk of lost or forgotten passwords
Note
- Enabling SAML will mandate all users to sign in only via SAML.
- Okta, Google and Azure AD are the supported IdPs. If you are using a different IdP, please raise a request to Fill support
- Only one IdP can be configured at a time.
- The team member's email address must be present in Fill and IdP.
Terminology
Team Member: Team Member is an employee of the organization, say, Acme Inc, and is an authorized user of Acme Inc's Fill User Interface.
Authentication: The verification mechanism that certifies an individual is the actual person they claim to be.
IdP: Identity Provider (IdP) is the platform or application that provides authentication for the member.
SP: Service Provider (SP) is the application that needs authentication for allowing access to the member. For the entirety of this doc, Fill is the Service Provider.
Login URL: This URL will take you to the IdP's login page asking for your credentials. Login URL is provided by your IdP and must be added in Fill while integrating.
X.509 Certificate: Fill accepts only X.509 Certificate to validate the authenticity of an IdP.
Login Options
You can log in to Fill using one of the ways listed below:
Sign in via IdP
- Log into your IdP.
- Select Fill from the list of applications.
- You will be taken to the Fill Dashboard.
Sign in via Fill
- In the login page, click Log in with SSO.
- Enter the email in the text box provided and click Sign in.
- You will be taken to your IdP's login screen. Enter your credentials and click Sign In.
Okta as IdP
You can add Fill app in Okta using the steps below:
- Log in to your Okta account and search for "Fill" under Add applications
- Enter your email name in the Subdomain field and click Done.
- Click View Setup Instructions under the Sign On tab to get the
- Login URL
- SAML Certificate
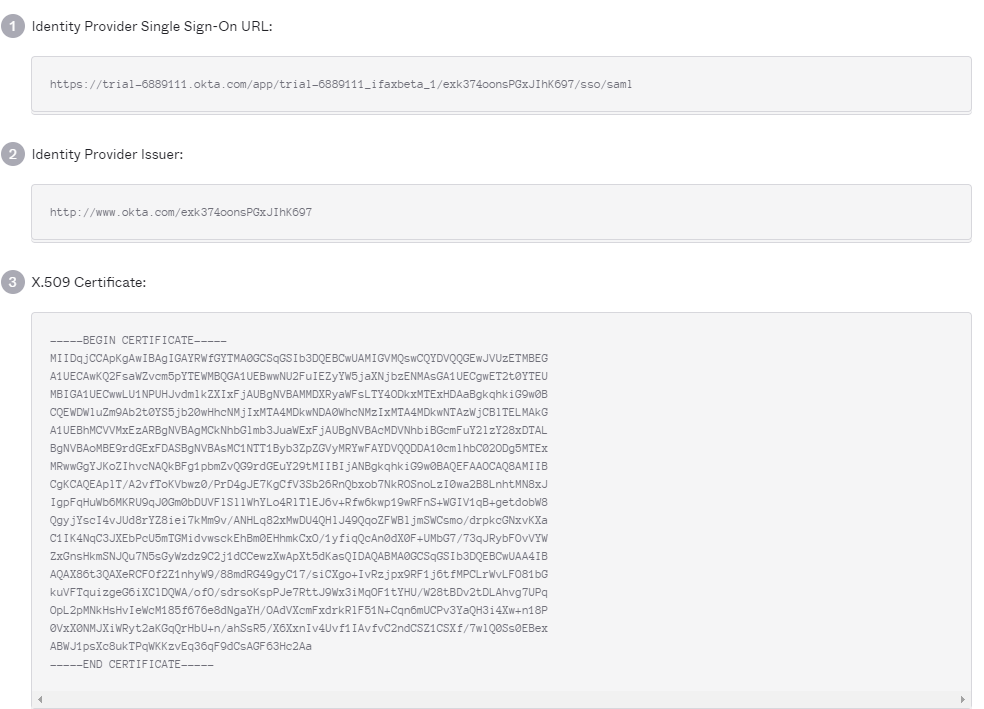
These are required and need to be pasted in your Fill User Interface while enabling SAML.
Google as IdP
You can add Fill app in Google using the steps below:
- Log in to your Google admin account and search for "Fill" under Add applications
- https://app.fillhq.com/login/ - for ACS URL(Assertion Consumer Service URL).
- https://app.fillhq.com/ - for Entity ID
- Click View Setup Instructions under the Sign On tab to get the
- SSO URL
- SAML Certificate
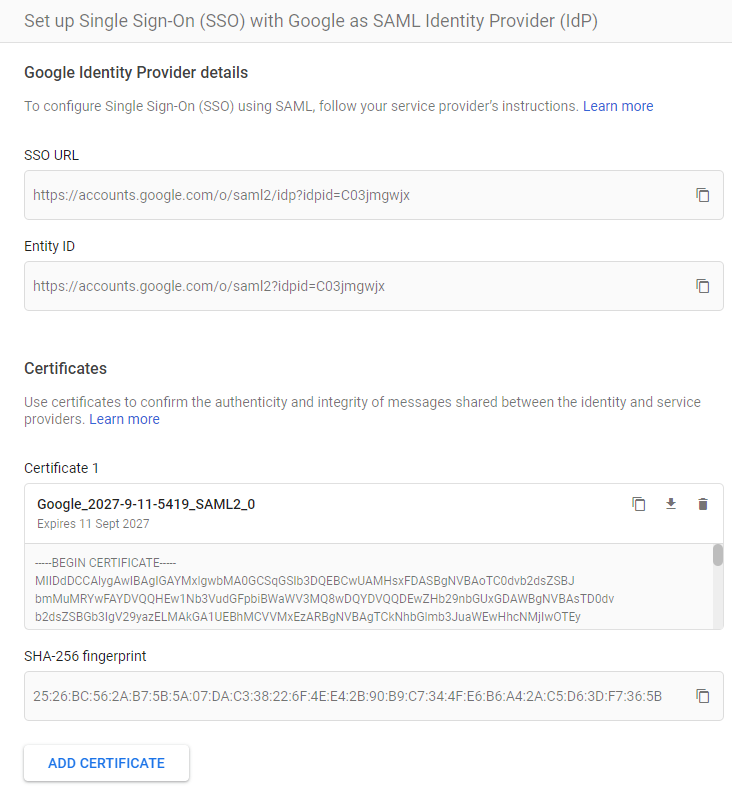
These are required and need to be pasted in your Fill User Interface while enabling SAML.
Azure AD as IdP
You can add Fill app in Microsoft's Azure Active Directory using the steps below:
- Sign into your Microsoft Azure site(through portal.azure.com).
- Go to Azure Active Directory > Enterprise applications > New application > Non-gallery application and add an application by naming it as "Fill".
- Now, go to the newly created Fill application and select Single sign-on found on the left pane and select SAML.
- Click edit against the Basic SAML Configuration section and enter
- https://app.fillhq.com/ - for Identifier(Entity ID) field
- https://app.fillhq.com/login/ - for Reply URL (Assertion Consumer Service URL) field.
- Scroll down to the Setup Fill section. Copy the Login URL and paste it in the field provided in Fill's SAML Configuration page.
- In the SAML Signing Certificate section, Use the URL given against App Federation Metadata URL and copy the content present between the start and end tags of «X509Certificate». Paste it in Fill's SAML Certificate field.
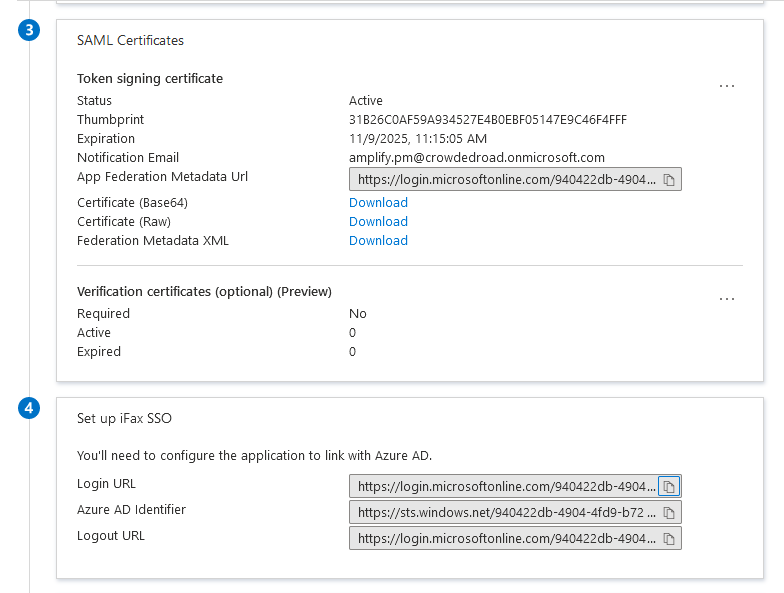
Configure SAML in Fill
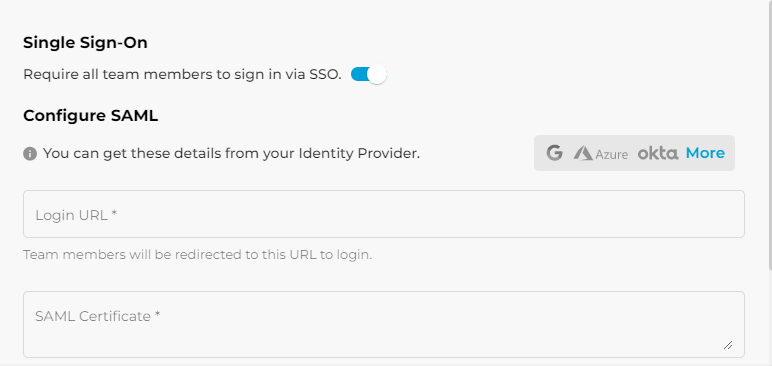
- Login to Fill and navigate to Settings > Team & SSO > SSO.
- Enable Single Sign On.
- Paste the Login URL and the X.509 Certificate retrieved from the IdP.
Disable SAML
To disable SAML, go to Settings > Team & SSO & SSO and disable Single Sign On.
When you disable SAML in Fill, your team members will be notified that SAML has been disabled and they should sign in using custom credentials.
Email Notifications
Your Team members will receive a system generated email during the following events:.
- When admin enables SAML for the organization's Fill site
- When a new team member is added to the organization's Fill site
- When SAML is disabled
